
by LVT_Admin | Jan 14, 2022 | News, Security, Structured Wiring, Technology, Technology News
SecurityInfoWatch.com recently caught up with several prominent industry analysts to get their take on which trends will continue to impact the physical security industry in 2022, In a year that saw many industries continue to be dogged by the Covid-19 pandemic in...

by LVT_Admin | Dec 8, 2021 | Fire, Fire Alarms, News, Technology
Fire Safety Smoke alarms and home safety Smoke alarms save lives. A smoke alarm is very important for keeping your home safe. You can die in a fire at home, especially at night or early in the morning when you’re asleep. More people die from breathing in smoke...

by LVT_Admin | Oct 25, 2021 | Business, Central Monitoring, contactless temperature scanner, News, People That Make A Difference, Security
Who could have guessed we’d be comparing contactless temperature scanners to a standard forehead thermometer—never in a million years! But, it is 2020, after all, and these crazy times continue challenging our everyday lives. “How can my business navigate through such...
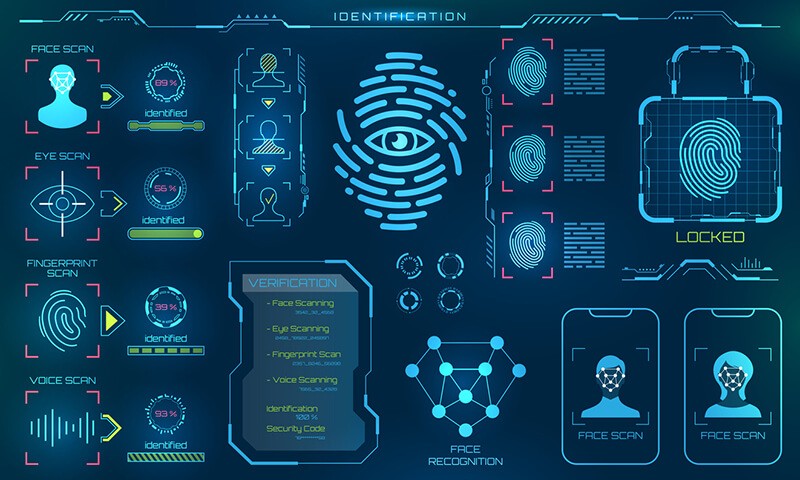
by LVT_Admin | Oct 18, 2021 | Access Control, Automation, Business, News, Security
The technologies behind physical access control are constantly evolving. Smart card technology is still the most common as it meets the needs of many organizations. But the steady stream of technological advances in access control means there are many new options...

by Liquid Video Technologies | Jul 21, 2021 | Cybersecurity, Data Breaches, Hacker, Malware, Network Security, Networking, News, Security, Websites, zero trust
Threat intelligence researchers from Google on Wednesday shed more light on four in the wild zero-day flaws in Chrome, Safari, and Internet Explorer browsers that were exploited by malicious actors in different campaigns since the start of the year. The four flaws...

by Liquid Video Technologies | Jun 2, 2021 | Cybersecurity, Data Breaches, Hacker, Malware, Monitoring, Network Security, News, Security, Security Breach, zero trust
U.S. President Joe Biden has signed an executive order, EO, to improve the cybersecurity of the U.S. As the U.S. faces persistent and increasingly sophisticated malicious cyber campaigns that threaten the public sector, the private sector, and ultimately people’s...








Recent Comments